Role of GPS Spoofing and GSM Hacking in Modern Era

This write-up is a part of HakTrak Cybersecurity Squad’s research activity.
بِسْمِ اللَّهِ الرَّحْمَنِ الرَّحِيمِ
1. Introduction
In this modern era, cyber attacks have seemingly become an inseparable phenomenon from our digital world. The close connection between various aspects of human life and the digital world, such as in communication, education, government and banking, appears to open opportunities for individuals or groups with malicious intent to carry out cyber attacks.
This historical intertwining of technology and security breaches itself seems almost inseparable since the occurrence of early cyber attacks. For example, the first recorded cyber attack technically occurred in France in 1834, when two thieves stole financial market information by hacking into the French Telegraph System.
Additionally, throughout the years, other “hackers” emerged to disrupt telephone and wireless telegraphy services. Then, in 1962, a significant milestone in cyber attack history was reached when Allen Scherr launched a cyber attack on the MIT computer network and stole passwords from their punch card database.
Furthermore, the evolution of cyber attacks seems to have moved beyond simple digital disruption, extending its reach into nearly all forms of warfare, including the realm of physical warfare (modern armed conflicts). For example, cyber operations can disrupt IT equipment, drones, or combatants’ GPS devices, thereby influencing military strategies and capabilities. In this context, techniques such as GPS Spoofing and GSM Hacking are also increasingly utilized to support military operations. This integration of cyber attacks into physical warfare highlights their growing significance and impact on global security landscapes.
With the increasing use of GPS Spoofing and GSM hacking across various scenarios, through this article, we aim to further discuss their historical evolution and development, as well as how these techniques are used in the context of cyber attacks and physical warfare.
1.1. The History
To understand the content of this article, we must first explain what GPS Spoofing and GSM Hacking in simple and basic terms.
1.1.1. GPS Spoofing
GPS Spoofing is a technique in which false signals or fake information is sent to a GPS receiver, causing it to believe that its location is in a place that does not actually exist. This technique aims to “deceive” devices that rely on GPS signals, such as autonomous vehicles or navigation systems, by providing incorrect information about their actual location or route. In reality, the use of GPS Spoofing is widespread, ranging from gaming to even warfare.
1.1.1.1. The Use of GPS Spoofing
In its early development, GPS Spoofing was initially designed for military use, and it was the military that first employed it.
Specifically in the context of military, GPS spoofing is employed as a strategic tactic to mislead enemy forces regarding their geographical positioning or intended routes. By transmitting false GPS signals, adversaries can deceive military assets, such as unmanned aerial vehicles (UAVs) or guided munitions, causing them to deviate from their intended targets or paths. This deceptive technique can significantly disrupt military operations by leading to inaccurate targeting or navigation errors, thereby undermining the effectiveness of enemy attacks or defenses.
So, when was GPS Spoofing first used? Honestly speaking, we haven’t found a source that specifically outlines the initial usage of GPS Spoofing. However, according to information from Digitalert, in 2011, there was a claim of a highly publicized case of GPS spoofing took place when Iran asserted that they had seized a U.S. RQ-170 Sentinel drone. As per reports, Iranian forces purportedly utilized GPS spoofing to manipulate the drone’s navigation system, guiding it to land within Iranian borders. This event underscored the practical consequences of GPS spoofing in geopolitical confrontations.
1.1.2. GSM Hacking
GSM hacking traces its origins back to the early days of telecommunications when a group of enthusiastic programmers known as the “phone phreaks” explored the telephone system to understand its inner workings.
Technically, GSM hacking is employed to manipulate communication systems regarding their network positioning or intended routes. By transmitting false GSM signals, adversaries can deceive communication assets, such as mobile phones or network systems, causing them to deviate from their intended targets or paths. However, when we discuss hacking mobile phone communication towers, it involves the ability to access all communications conducted via mobile phones, including calls or SMS messages. Additionally, the hacker can obtain more information through the IMSI, which is analogous to the MAC Address in NIC.
From the reference that we obtained, one of the earliest instances of this kind of hacking can be traced back to the 1960s, when a group of students at the Massachusetts Institute of Technology (MIT) stumbled upon a method to make free long-distance phone calls using a device dubbed a “blue box”. Some people said that this occurrence highlights the real-world impacts of GSM hacking within telecommunication systems.
2. The Technical Details
Some of you may be wondering, how exactly do these two things work? In this section, we will try to examine how the process works from the client’s perspective first.
2.1. Understanding GPS Spoofing Mechanism
In the context of GPS, signals are transmitted across three main frequency bands, namely L1, L2, and L5. Each frequency band serves specific purposes and comes with its own set of characteristics. Here’s a simple highlight of this:
- The L1 Frequency is transmitted at 1575.42 MHz and is used for civilian purposes. It carries the civilian GPS navigation message which is used by GPS receivers to determine their location. This frequency band is susceptible to interference and can be jammed or spoofed, although countermeasures can be implemented.
- The L2 Frequency is transmitted at 1227.60 MHz and was originally used for military purposes. It is more secure and has enhancements against signal spoofing and jamming. However, modern GPS receivers, especially those used for high precision applications like surveying, can use both L1 and L2 frequencies to improve accuracy.
- The L5 Frequency is transmitted at 1176.45 MHz and is part of the modernization efforts of the GPS by the US Department of Defense. This frequency has unique properties that make it more suitable for certain types of applications. For example, the L5 frequency is used to improve accuracy for civilian uses such as precision aircraft approach guidance.
Despite their initial civilian and military designations, the lines between L1 and L2 frequencies have blurred over time due to technological advancements and policy changes. For example, modernized GPS signals now include civilian signals on the L2 frequency (L2C) and military signals on the L1 frequency (M-code).
In the military sector, both L1 and L2 frequencies are utilized, with information transmitted from military satellites being encrypted to prevent unauthorized access. Technically these satellites can be used for various purposes, including guiding ballistic and intercontinental missiles, drones, unmanned aerial vehicles, etc.
2.1.1. HackRF One for GPS Spoofing
Some of you might have heard of HackRF. HackRF is a flexible tool used for various Radio Hacking activities, offering multiple types to suit different needs, which one of them is HackRF One. This type of device was then customized by OpenSourceSDRLab to have broader capabilities (and named HackRF One & PortaPack H2 — which we will discuss in this article).
Specifically, the HackRF One & PortaPack H2 has the ability to boast a wide frequency range from 1MHz to 6GHz, making it well-suited for Radio Hacking activities, including those involving GPS signals. With this broad range coverage, the HackRF One & PortaPack H2 can intercept and manipulate signals across various GPS frequencies, enabling a range of activities, from tracking airplane flights using the ADS-B system to executing WiFi or GSM jamming.
Moreover, the HackRF One & PortaPack H2’s open-source system provides access to a wide range of attacks for transmitting and receiving signals. This flexibility makes it an invaluable tool for Radio Hacking activities, encompassing tasks such as GPS spoofing and signal manipulation.

Technically, this device is capable of simulating various operations, including GPS Spoofing. The range of its capabilities can vary based on the environment surrounding the test site, as radio waves are greatly affected by physical objects that could obstruct them. One thing that can enhance the range of radio wave transmission is a Radio Amplifier, but it is important to consider that an amplifier supports specific frequencies, etc.

2.1.1.1. GPS Spoofing with HackRF One & PortaPack H2
To use the HackRF One & PortaPack H2 for GPS spoofing, we need to enhance the HackRF One with the necessary files containing the coordinates to spoof. The question might arise, how can we obtain this file?
Firstly, we need to download the gps-sdr-sim tool from this Github repository: https://github.com/osqzss/gps-sdr-sim.
After downloading this tool, we need to acquire another file from NASA, which is a GPS satellite ephemeris and clock data file. Both of these files are essential for the gps-sdr-sim tool to generate realistic fake GPS signals.
An Ephemeris is a set of data that provides the precise position of a satellite in its orbit at a specific time. On the other hand, the satellite clock data provides information about the internal time offset of the satellite compared to GPS time. By using this data, gps-sdr-sim can generate GPS signals that closely resemble the actual signals sent by GPS satellites. This allows the target GPS device to receive these signals as if they were coming from the original GPS satellites, thus enabling GPS location spoofing.
So, where can we get this file? Technically, we can obtain this from the following link: https://cddis.nasa.gov/archive/gnss/data/daily/2024/brdc/.
Please note that the site requires us to log in. If we don’t have an account, we just need to create a new one, verify it, then return to the same link and download the file ending with “.24n.gz”, regardless of the year we are applying the step. Even if it’s 2025, just select the year, scroll down to the “brdc” file, and then check the file extension.
After downloading it, extract the file from the compressed archive.
Once these steps are completed, return to the gps-sdr-sim directory and execute the necessary commands to extract the required file:
./gps-sdr-sim -e brdc0010.24n -s 15754200 -b 8 -o gpssim.C8 -l **.*****,**.******,100 -d 100
To understand the commands and options we selected, you can type the tool name with -h:
./gps-sdr-sim -h
Let’s say we have obtained the file. The next thing we have to do is transfer it to the SD card of the HackRF One PortaPack H2, specifically into a folder named GPS.
After transferring the file, turn on the HackRF One and navigate to the following menu: “Transmit > GPSSim > Open file > Start”.



From here, we can change the frequency inside the HackRF One to target the desired satellite.
Note: We disclaim any responsibility for any unethical or illegal use of the content written in this article.
2.2. Understanding the Concept of GSM Hacking Techniques
In the realm of mobile communication, each mobile SIM across the globe is equipped with a unique identifier known as the International Mobile Subscriber Identity (IMSI). The IMSI is a number that uniquely identifies every user of a cellular network. It is stored as a 64-bit field and is sent by the mobile device to the network.
In its implementation, the technical composition of an IMSI is divided into three parts, namely:
- Mobile Subscriber Identification Number (MSIN): Typically has 9 to 10 digits, depending on the length of the MNC. The MSIN identifies the subscriber in the network’s customer database.
- Mobile Country Code (MCC): Consists of 3 digits and identifies the country of the mobile device.
- Mobile Network Code (MNC): With 2 or 3 digits, the MNC identifies your operator’s network within that country.
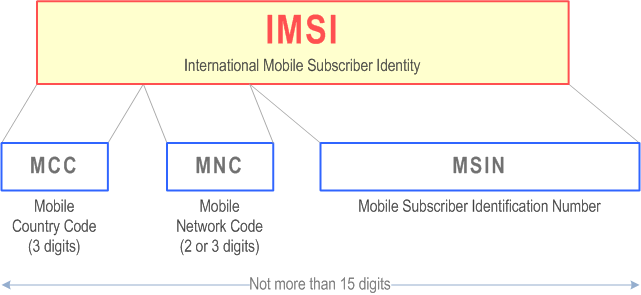
The IMSI is used in any mobile network that interconnects with other networks. For GSM, UMTS, and LTE networks, this number is provisioned in the SIM card and for cdmaOne and CDMA2000 in the phone directly or in a R-UIM card (CDMA equivalent of a SIM card).
Please note that your IMSI is not our IMEI number even though both are sent to our cellular operator and registered in the network. The IMEI is a unique element of our phone’s hardware.
Technically, the IMSI is used by the network to identify and track mobile devices within the operations of GSM towers, which operate at frequencies ranging from 900 to 970 MHz. However, there is a slight issue. These frequencies of GSM towers “allow” even a basic radio receiver to intercept communications. For example, the RTL-SDR v3, which can cover a range from 500 MHz to 1.72 GHz, is more than adequate for such tasks. This highlights the potential security concerns in mobile communications.
2.2.1. The Tools
Given the potential security concerns from the situation we have conveyed, at this stage, we will attempt to explain how one can intercept cellular phone traffic.
In this specific area, there is a popular tool among researchers and enthusiasts that called grgsm (https://github.com/ptrkrysik/gr-gsm). This tool provides several utilities, such as grgsm_scanner, which scans and searches for the frequencies of communication towers. Additionally, there’s also grgsm_livemon, which allows users to listen to all communications over the previously identified.

So, let’s say we aim to test this kind of issue with cell phone communication towers. The first thing we need to do is identify the frequencies and available channels of the towers. To do this, they can use a tool called kalibrate-rtl, which can be installed with the following command:
apt install kalNote: execute
kal -hto see the available options, as shown in the picture below:

After installing the tool, we should check if the radio frequency device is connected to the same system (by using lsusb).

As a proof of concept, in our lab, we use the rtl-sdr v3 (and of course, other more effective tools can also be used to identify the available channels and frequencies).
In the second step, we need to run the command of -s with the selected band. This command will allow us to identify the frequencies and channels in our area.
kal -s GSM900
In the third step, we need to execute the grgsm_livemon tools. This tools is basically used for listening to radio signals.
grgsm_livemon -f 943.6M -g 40
Please note that there are many other tools in the same package, such as
grgsm_decode, but we won't cover in this article as it requires a separate detailed guide.
After it starts running (listening to the signals), we need to launch Wireshark (for better data monitoring) to monitor all traffic passing between the device and communication towers, and vice versa — with the following command:
wireshark -k -Y '!icmp && gsmtap' -i lo
This allows us to eavesdrop on all communications with the GSM tower. In the illustrated picture, we can see that we captured a connection from a user connected to the network.

Please note that as an additional step, we can also run the IMSI Catcher (https://github.com/Oros42/IMSI-catcher) tool to capture IMSI and other information using this command:
python3 simple_IMSI-catcher.py -s
3. Conclusion
Although the technical concepts discussed in this article are still basic, GPS spoofing and GSM hacking are not merely technical phenomena but common strategic moves used in the digital battlefield. The impact of these technologies reverberates globally, challenging the integrity of our communication infrastructure.
This article not only provides an overview of academic journey but also serves as a strong call to enhance our vigilance and fortify our defenses against the invisible arrows of the modern age.
4. References
- Monroe College, “CYBERSECURITY HISTORY: HACKING & DATA BREACHES,” [Online]. Available: https://www.monroecollege.edu/news/cybersecurity-history-hacking-data-breaches. [Accessed 08 May 2024].
- M. Schulze, “Cyber in War: Assessing the Strategic, Tactical, and Operational Utility of Military Cyber Operations,” in 2020 12th International Conference on Cyber Conflict, Tallinn, 2020.
- B. Ben, “Why GPS spoofing is a problem (and what to do about it),” 12 November 2020. [Online]. Available: https://nextnav.com/gps-spoofing/. [Accessed 09 May 2024].
- digiALERT, “Understanding GPS Spoofing: A Comprehensive Overview,” 15 December 2023. [Online]. Available: https://www.digialert.com/index.php/blog/item/231-understanding-gps-spoofing-a-comprehensive-overview. [Accessed 09 May 2024].
- Blue Goat Cyber, “A Comprehensive History and Evolution of Hacking,” [Online]. Available: https://bluegoatcyber.com/blog/a-comprehensive-history-and-evolution-of-hacking/. [Accessed 09 May 2024].
- Tech-Invite, “Composition of IMSI,” [Online]. Available: https://www.tech-invite.com/3m23/toc/tinv-3gpp-23-003_b.html. [Accessed 10 May 2024]
- Mayhem, “PortaPack Mayhem,” [Online]. Available: https://github.com/portapack-mayhem/mayhem-firmware/wiki/GPS-Sim.
- International Numbering Plans — https://www.numberingplans.com/?page=analysis&sub=imsinr
- OSQZSS, “GPS-SDR-SIM,” [Online]. Available: https://github.com/osqzss/gps-sdr-sim
- https://cddis.nasa.gov/archive/gnss/data/daily/2024/brdc/
- K. Piotr, “The gr-gsm project,” [Online]. Available: https://github.com/ptrkrysik/gr-gsm
- Oros, “IMSI-catcher,” [Online]. Available: https://github.com/Oros42/IMSI-catcher
5. Disclaimer
It’s important to note that while this article provides information on some techniques, it does not endorse or encourage unethical or illegal activities. The tools and methods discussed should be used responsibly, adhering to all applicable laws and regulations. Misuse can lead to serious legal consequences. The aim of this article is to increase awareness and understanding of these techniques, contributing to the development of more secure and resilient systems.
The authors disclaim any responsibility for any unethical or illegal use of the content.
Hopefully, the knowledge learned can be utilized as well as possible for the right purpose.

